covert chanel | covert channel through cloud storage covert chanel In computer security, a covert channel is a type of attack that creates a capability to transfer information objects between processes that are not supposed to be allowed to communicate by the computer security policy. The term, originated in 1973 by Butler Lampson, is defined as channels "not intended for . See more Năm 2023, hãng LV hứa hẹn sẽ “khuấy đảo” giới mộ điệu với những sản phẩm giày nam Louis Vuitton cực kỳ ấn tượng. Giày da nam Louis Vuitton, giày hàng hiệu Louis Vuitton. Hãy cùng Duvis khám phá điều này nhé. Tổng quan về giày da nam Louis Vuitton. Louis Vuitton ra đời như thế nào? Được thành lập vào năm 1854 và có trụ sở tại .
0 · what is covert channel analysis
1 · types of covert channels
2 · covert channels in cyber security
3 · covert channels examples
4 · covert channel vs side channel
5 · covert channel through cloud storage
6 · covert channel meaning
7 · covert channel definition
Top sản phẩm Giày sneaker bán chạy. Giày sneaker Diadora Giày sneaker PUMA cho Nữ Giày sneaker New Balance cho Nữ Giày sneaker Dockers Giày sneaker Li-Ning Giày sneaker Bally Giày sneaker Polo Giày sneaker Vans Giày cổ thấp Champion Giày slip on adidas. Mua online @Cửa hàng trực tuyến Louis Vuitton Việt Nam .
In computer security, a covert channel is a type of attack that creates a capability to transfer information objects between processes that are not supposed to be allowed to communicate by the computer security policy. The term, originated in 1973 by Butler Lampson, is defined as channels "not intended for . See more
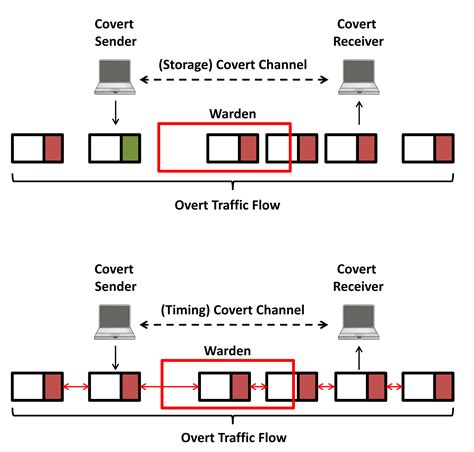
A covert channel is so called because it is hidden from the access control mechanisms of secure operating systems since it does not use . See moreThe use of delays between packets transmitted over computer networks was first explored by Girling for covert communication. This . See moreThe possibility of covert channels cannot be eliminated, although it can be significantly reduced by careful design and analysis. See moreAs Girling first analyzes covert channels in a network environment. His work focuses on local area networks (LANs) in which three obvious covert channels (two storage channel and . See more
Ordinary things, such as existence of a file or time used for a computation, have been the medium through which a covert channel . See moreHandel and Sandford presented research where they study covert channels within the general design of network communication . See more
what is covert channel analysis
Focusing on the IP and TCP headers of TCP/IP Protocol suite, an article published by Craig Rowland devises proper encoding and decoding techniques by utilizing the IP . See more A covert channel is a type of computer attack that allows the communication of information by transferring objects through existing information channels or networks using the .A covert channel is a logical channel used for sending hidden messages by leveraging information hiding technology over a public channel. Its establishment is crucial for an information hiding .
What Are Covert Channels? A covert channel is defined as: A type of computer attack that allows the communication of information by transferring objects through existing .A covert channel is a method of communication that is used to transfer information secretly and evade detection by an antivirus or other security measures. It is often used by hackers to . A covert channel is a channel that is hidden. This means that its existence is intentional, and additionally there is an intention to conceal or hide its existence from a person . In computer networking, Covert channels hide the communication or bypass any prevention mechanisms. In this way, any equipment listening to the network cannot detect the .
A covert channel is an information flow mechanism within a system that is based on the use of system resources not normally intended for communication between the users of the system. .
In computer security, a covert channel is a type of attack that creates a capability to transfer information objects between processes that are not supposed to be allowed to communicate by the computer security policy. A covert channel is a type of computer attack that allows the communication of information by transferring objects through existing information channels or networks using the structure of the existing medium to convey the data in small parts. DNS covert channels can be used to bypass a Wi-Fi paywall to avoid paying a service fee, or to run an unapproved application from a work computer. They can also be used to tunnel other Internet protocols such as Secure Shell, IP or even Tor.
A covert channel is a logical channel used for sending hidden messages by leveraging information hiding technology over a public channel. Its establishment is crucial for an information hiding system, as the discovery or disruption of the covert channel can . What Are Covert Channels? A covert channel is defined as: A type of computer attack that allows the communication of information by transferring objects through existing information.
A covert channel is a method of communication that is used to transfer information secretly and evade detection by an antivirus or other security measures. It is often used by hackers to bypass security measures and steal sensitive information. A covert channel is a channel that is hidden. This means that its existence is intentional, and additionally there is an intention to conceal or hide its existence from a person who is trying to protect the system by filtering or limiting data flow. In computer networking, Covert channels hide the communication or bypass any prevention mechanisms. In this way, any equipment listening to the network cannot detect the presence of a.A covert channel is an information flow mechanism within a system that is based on the use of system resources not normally intended for communication between the users of the system. Storage Channels use system variables and attributes (other than time) to .
A covert channel is a communication channel that allows entities to transfer information in a way that violates the system's security policy. While these channels can increase the privacy and security of critical communication, criminals use covert channels to carry out cyberattacks.
In computer security, a covert channel is a type of attack that creates a capability to transfer information objects between processes that are not supposed to be allowed to communicate by the computer security policy. A covert channel is a type of computer attack that allows the communication of information by transferring objects through existing information channels or networks using the structure of the existing medium to convey the data in small parts.
DNS covert channels can be used to bypass a Wi-Fi paywall to avoid paying a service fee, or to run an unapproved application from a work computer. They can also be used to tunnel other Internet protocols such as Secure Shell, IP or even Tor.A covert channel is a logical channel used for sending hidden messages by leveraging information hiding technology over a public channel. Its establishment is crucial for an information hiding system, as the discovery or disruption of the covert channel can .
What Are Covert Channels? A covert channel is defined as: A type of computer attack that allows the communication of information by transferring objects through existing information.
A covert channel is a method of communication that is used to transfer information secretly and evade detection by an antivirus or other security measures. It is often used by hackers to bypass security measures and steal sensitive information.
A covert channel is a channel that is hidden. This means that its existence is intentional, and additionally there is an intention to conceal or hide its existence from a person who is trying to protect the system by filtering or limiting data flow. In computer networking, Covert channels hide the communication or bypass any prevention mechanisms. In this way, any equipment listening to the network cannot detect the presence of a.A covert channel is an information flow mechanism within a system that is based on the use of system resources not normally intended for communication between the users of the system. Storage Channels use system variables and attributes (other than time) to .

types of covert channels
53K Followers, 2,649 Following, 2,224 Posts - Gold and Beyond | Las Vegas (@goldandbeyond) on Instagram: "The BIGGEST Kept Secret. 🤫👑 #1 in Authentic Luxury Resale 376 W Sahara @ Las Vegas Blvd 🌴 OPEN 24 HOURS (702) 396-3333".
covert chanel|covert channel through cloud storage